SUIM: Check user access
This is the last two really basically about user access. So we often want to do a lot of analysis about user access and I love doing analysis about user access. I’ll tell you why, because it actually costs a fortune.
Like when people doing analysis on user access, they can pay a fortune for SAP GRC. And the problem with it is, it’s only as good as the actually put it in place, right? So if you’re doing some like SAP GRC or you’re using SAP GRC for looking at user access, but the SAP GRC system is not set up for all the users or for all of the conflicts or all the transaction codes or something like this, like lots of different ways it can go wrong, then you might not see everything. So as an auditor, you might, if you like doing that kind of thing, you find it quite funny, you might want to do some SAP transaction code, like separation, like you want to see who has access to what basically in the SAP system.
And it’s quite a fun exercise. It’s also really complicated to do, like it took us like three or four months to do it ourselves. But once you’ve done it, you’ve done it and then you can like rerun it. But when you run these kind of analysis, it’s a quite complicated, like you’ve got this whole concept here about roles and authorities and objects and things like that. And you can find I can find out quite easily who’s got which transaction codes, but they don’t necessarily be able to use the transaction code, even if they’ve got it, because they need the specific object to use it on. Or it might be that they’ve got a transaction code in one company and they don’t have it in another company.
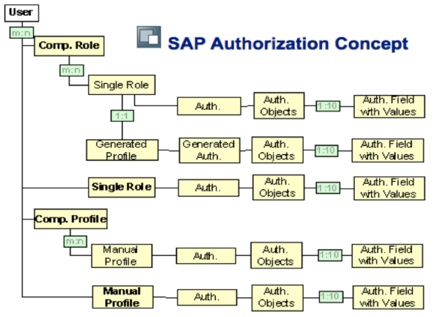
So they can’t do the conflict within the same company. And so it’s not really that much of an issue. So it’s quite complicated to compute. So once we have computed it, we always want to double check, right? We want to double check. So we want to be able to use SUIM. It’s very easy to use.
It basically lets you to look up users, look up roles, look up authorisations, check which users have got which transaction codes and all these things. But it only actually will do it. I mean, it’s quite basic.
Obviously, it’s not as good as SAP GRC. Otherwise, no one would buy SAP GRC, right? So it’s going to let you do it user by user or like transaction code by transaction code. But it’s really good if you’ve got a dashboard about separation of duties and you want to just check something.
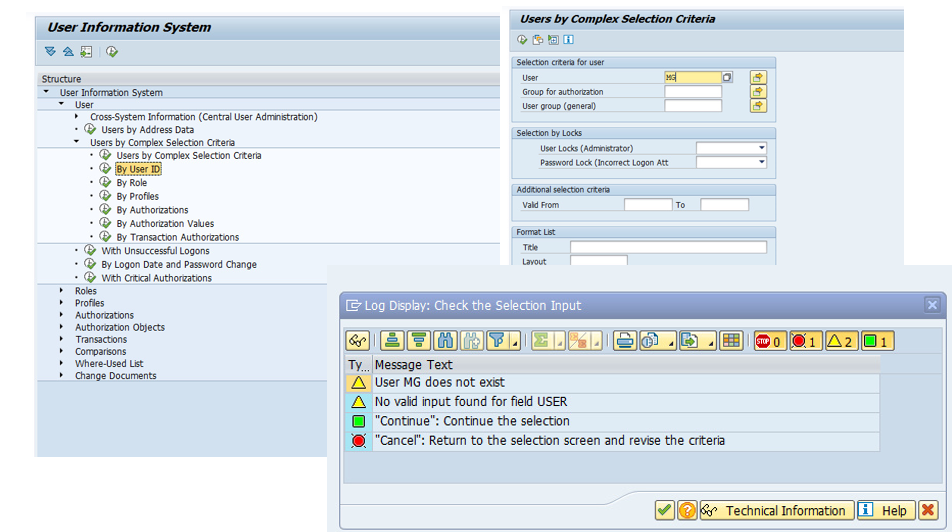
So for us, what we want to do is we had our funny user, MG. And our MG user, we want to see, like, what does this person do? You know, like, you know, has he got access to loads of stuff? Who is he? Stuff like that. So typically, we quickly do an SUIM just to find out what this user’s normally got access to. Like, what’s their role? What’s their thing? So I’m going to go into SUIM and click on by user ID. And then I can type in my user. And actually, what we find is that this user doesn’t exist anymore. And it could be, you know, like, it was a temporary user, or somebody who’s left the company, like transactions looking at kind of old. So that might be why. But they don’t actually exist anymore.
All right, so it would be even better. Here is just a little pitch for our upcoming webinar that we’re going to do soon, is it would be so much easier, though, if you could just have a dashboard about like all of the purchase to pay process. And if you’ve got somebody, you think this user is a little bit strange, you know, they’re doing little strange stuff.
And you want to see everything that that particular user does. And if that’s the case, it would be really cool if you had what we call process mining dashboard. And process mining is like, it’s actually for helping you to see how data flows for your SAP system, you know, like, do the patrol is then lead to invoice, then lead to payments? Or is it like you got the invoice first, and then the purchase order and things in the wrong order and stuff like that.
But once you’ve actually already got all your flows of the purchase to pay process, it’s very easy to then say, filter all those flows on a particular user or or something, in order to see everything that that user did, and all the flows that that user is involved in. So that’s something which will be coming up. And it’s really useful.
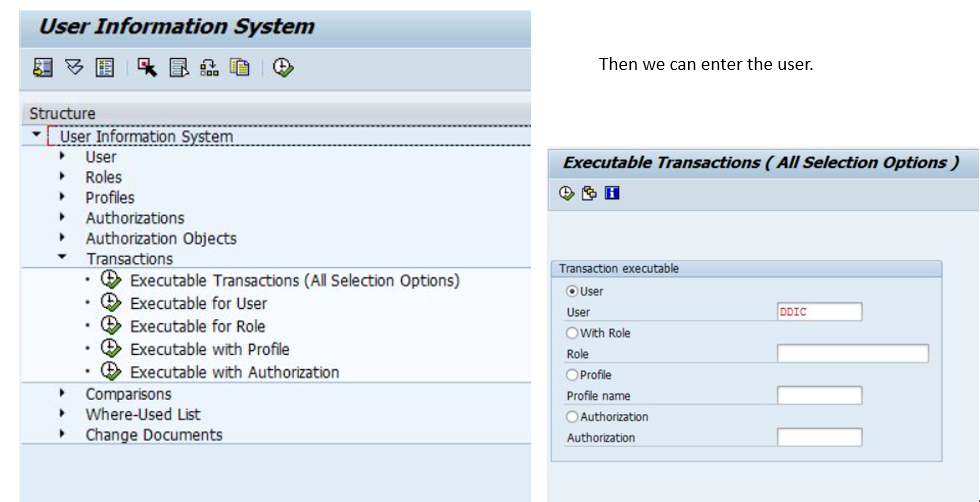
These days, everyone can do it is, you know, you don’t, you don’t need to be like super special, like super special system to do it is, you know, something attainable for auditors, and it really useful to use. So if we want to know what transaction codes that people are using, we can go to transactions, and we can look at what they can do and get that obviously, as you I am. So if you think that someone’s got too much access for their transaction codes, this is where you go and you look them up. And if MG did have still access the system, then this would be where we would check what they’ve got access to.
