Top 10 Data Analytics for Fraud Detection – Part 3
Fictitious suppliers is also really important,...
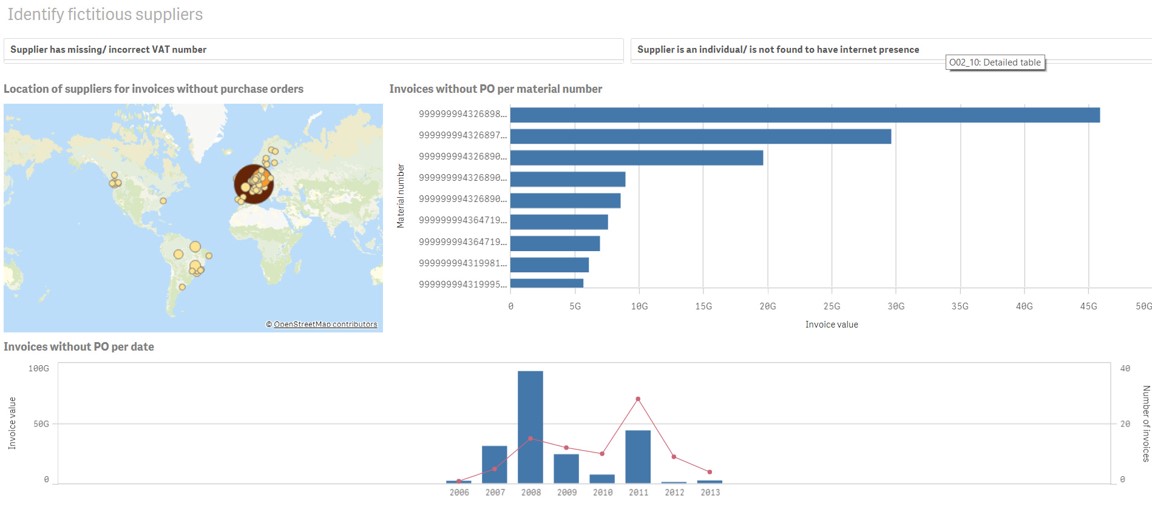
So here, you can see probably on our head office is somewhere in Europe, and because it’s big, great big splodge there for those ones. But what we want to look for is, you know, things like does our suppliers have missing information, like, or do they have incorrect VAT number. And this is something that we would typically use, like Python programme to look up if they actually exist online, or if their VAT number is incorrect, we can use a macro Python programme to look them up on government website or something.
So if I click on Yes, here, I can see that our internal control is actually really poor, because everyone doesn’t seem to have VAT number. So that’s not good. And then I can also use a Python programme to check if the supplier sounds like an individual, like is does the name of the supplier sound like a person.
If you use Python to do that, it’s really easy. And you can also use Python to check if they have a website. So typically, what we do is we go through, you know, if there’s like 40,000 suppliers in the database, we go through each one, the Python programme overnight, and it’ll load them all up in Google. It will see like, you know, what are the first five results for that particular supply name in Google, and then it will do a scoring. And if it finds nothing that resembles it whatsoever, then it flags them for us so that we can actually have a look and we have a look at the ones that don’t have internet presence. And so those will be the ones that we want to look at.
So if we find that it doesn’t have internet presence, and then it also doesn’t have any purchase orders for things that we’d expect it normally to have, then we might want to, you know, click a little bit more around and see where these people are. And it might be like, obviously, because you might be thinking, well, I don’t have suppliers over here in South America. So that’s maybe someone just doing something offshore.
So this is also a type of dashboard, we want to look for fictitious suppliers. Next one, we’re going to go back to Power BI now. And this one’s super exciting, because it’s about process mining. So with process mining, you can do so much. You can find out so many things. But actually, what I’m just going to talk about is users that violate access control and show you this really quickly.
So with process mining, you can do so much. And you can find out so many things. But actually, what I’m just going to talk about is users that violate access control and show you this really quickly.
So somebody at Sonosid, which is a mine in Morocco, said to me a really long time, it was 10 years ago, is one of our first clients. And he said to me, you know, I want to see the entire P2P process in one page. And at that time, I was like, oh my god, how do you do that? And it was just so hard.
I spent all night for a whole week of like, just all night long, like trying to work that out. And 10 years later, we’re still doing it. So we’re doing process mining. Process mining really is the thing these days, you know. So what do we do with process mining? Basically, we’ve got all of these different types of documents, and we superimpose them over each other over time. And that helps us to see, first of all, like whether or not our data looks correct. But also, once we’ve got all of that information in what we call like a process flow, you can see a process flow down here, you’ve got your purchase order, you’ve got the release, that’s the approbation, the goods receipt, everything’s looking normal. This is our normal flow, right? And then you’ve got people, because you’ve got the flow, within that flow, you can actually look at whether or not people are violating your user access. So what we want to do is to see if we’ve got user access violations.
So either we can click in this graph, there’s one down here that I like to look at all the time. It’s like, do we enter the invoice and the payment? Because that’s, you know, nobody should be doing that. So if I click on that one, first of all, I can see straight away above, you know, when is it happening? And how much is it happening? So is it happening all the time? And then in my process diagram down the bottom, I can actually see whether or not things are happening in the expected order.
So this one, you can see it’s not, it might be a down payment. But even so, it, you know, it should be, it shouldn’t be the same person entering it. And we do like to see whether or not things happening in the same order, like if you’ve got the PO approval happening after the goods receipt, that’s not good, right? So things like that.
Process mining is really good one to be able to have as one of your top 10 data analytics for detection, because you can just detect so much stuff. And if you have people that have too much access, then your company is just wide open anyway. All right, what about shell companies then? So we talked about shell companies earlier, because that is also part of the bidding scheme on the fraud tree.
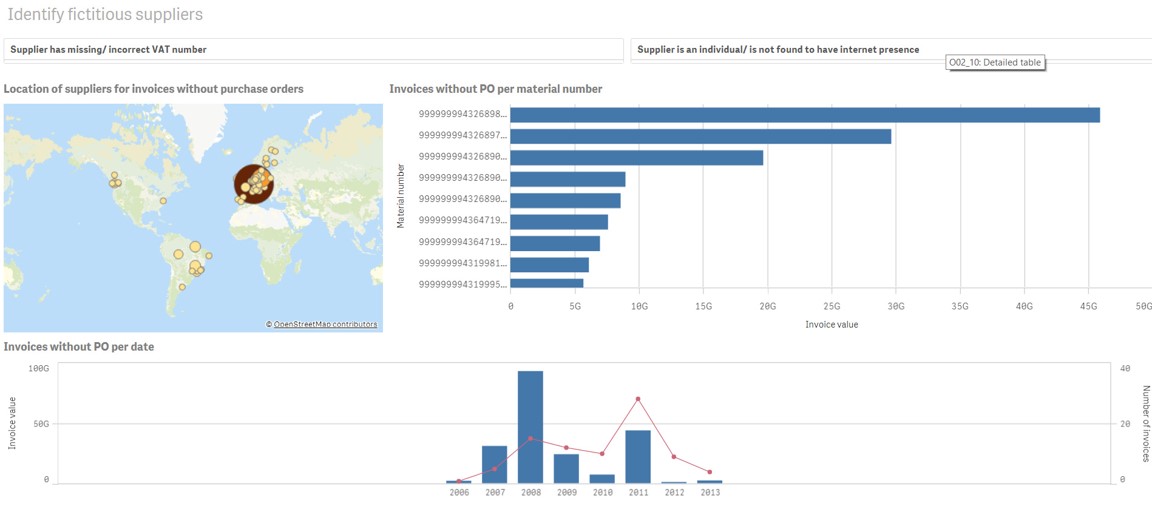
I probably don’t need to go into these dashboards, because they’re just tables. But typically, you definitely want to compare your employee’s address to your supplier’s address, employee telephone number, supply and telephone number, your bank accounts of employees, the bank account suppliers, like don’t let anyone tell you that you can’t do that because GDPR. If you’re an internal audit, you just you need to make sure that you’re able to do these things, maybe you actually, you know, hide the name of people, you can encrypt it, you can do a one for one encryption in SQL or ACL or something, if you really need to.
But this is a key one, you really want to make sure you don’t have any side businesses going on in your company. And then we want to look at non compliance vendor, that was another one in the billing part of the fraud tree. And for this one, we want to look at changes.
So we talked about changes earlier, changes are really important. And here, we’ve got an example of a change typically look at. So you can see for Anfluss Delta is a German company, they changed their somebody has changed their bank account details, and to from 212 to 967. Then they’ve changed it back again, from 967 to 212. So this is what we call flip flop IBAN. And when we do these kind of tests, we want to check whether or not there was a payment happening between the dates that we actually did the change.
So if someone did the change really quickly, and there was a payment also happening, then that is something key that we’re always looking at. Everyone’s always asked me to do that.
Then personal purchase is the last one on the billing part of the fraud, fraud tree.
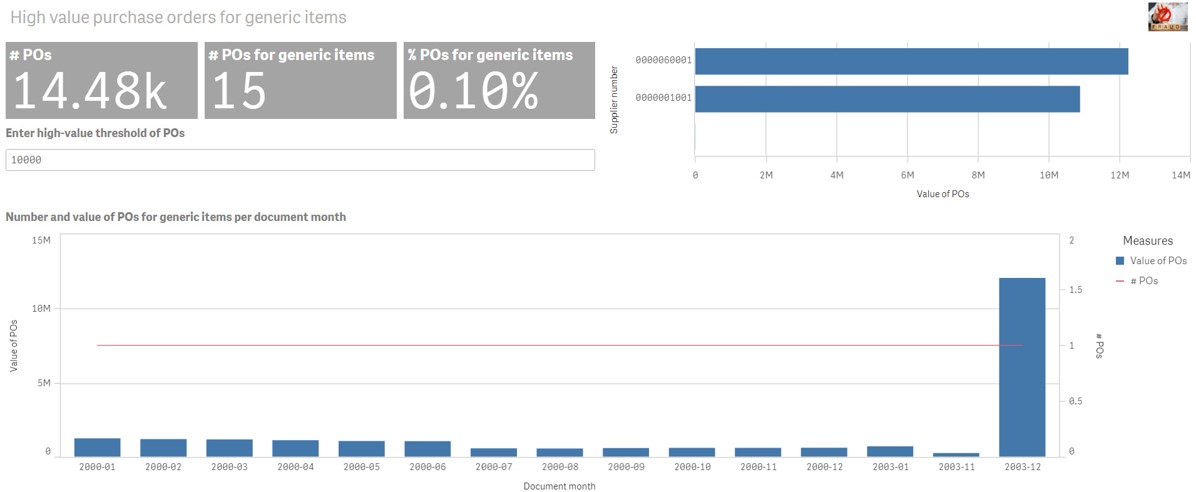
And for this one, here, you can see that you’ve got POS for generic items. So I’m calling this like personal purchase, but it’s like, actually, what we’re looking for is things that we shouldn’t normally purchase a really easy way to start, just look at generic items, you know, like, someone’s buying $10 million of consulting, and they’re not even bothering to say what kind of thing it is, or just training, or they might just say widgets or something like that. Or they might even not bother putting the material number at all.
So we call this generic. So you can also use machine learning to go through your list of materials, if you’ve got too many, and look for things that look too generic, okay. And you can put a threshold.
So we select high value generic items. And if you want, you can have a threshold. So you might like, you know, this one is over a million.
So if I change this 500 value here to 1 million, then you’ll see that I only get the result for 1 million. So that’s just to show you that you can actually have these threshold things on the dashboard. And that can actually help you to focus on the stuff that you really need to focus on.
The last one is employee indicators. We did see at the beginning on that heat map that there was payroll right in the middle. And so employee indicators is something quite key that we want to look at, for sure, right, because people always think payroll fraud is quite easy. And we do tend to leave payroll all alone, because we say it’s GDPR, and we cannot look at them.
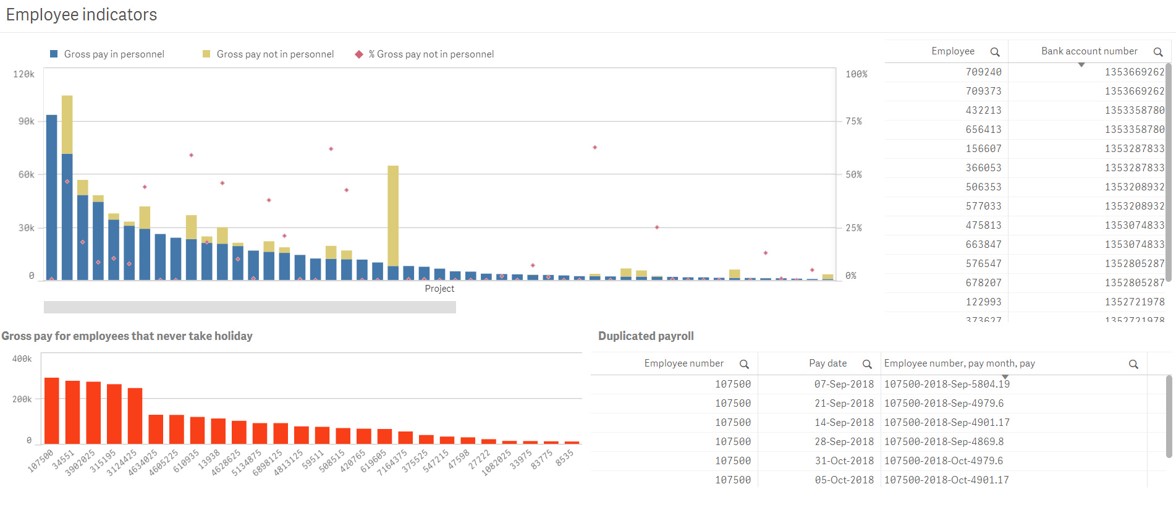
But you do want to look at them. So we want to look for ghost employees. So if we’re having ghost employees, typically we are having people that are not in personnel, but they could be not in personnel, not in your IT list, or not in the list of people who come into the building, could be lots of different things.
You get creative about what can you compare your payroll list to. And we also compare it typically to holidays, because if somebody creates a ghost employee, they’re probably not going to send them on holiday. Alright, so if I click on this bar here, you can see I’ve got a particular project going on where there’s loads of people that are not in personnel.
So maybe we outsourced it or something, and what we did, but or somebody’s lying about the cost of that project, because all those people are not on the personnel list, and might not even be on the timesheet list. And also, they are never taking holiday. And we can also see that for some of them up here, we’ve got employees actually sharing bank account numbers.
So, you know, it could even be that you have employees where somebody’s sharing a bank account number, because they’re just creating lots of fictitious employees, so they can get the money. And there’s another type of test that you can do also is just looking at the payroll values, and check whether or not you have any duplication down here.
